New Windows Search zero-day added to Microsoft protocol nightmare

A new Windows Search zero-working day vulnerability can be used to routinely open a research window made up of remotely-hosted malware executables simply by launching a Term doc.
The stability issue can be leveraged since Home windows supports a URI protocol handler identified as ‘search-ms’ that lets programs and HTML backlinks to start personalized queries on a device.
Although most Home windows lookups will glimpse on the community device’s index, it is also attainable to force Home windows Look for to question file shares on distant hosts and use a personalized title for the research window.
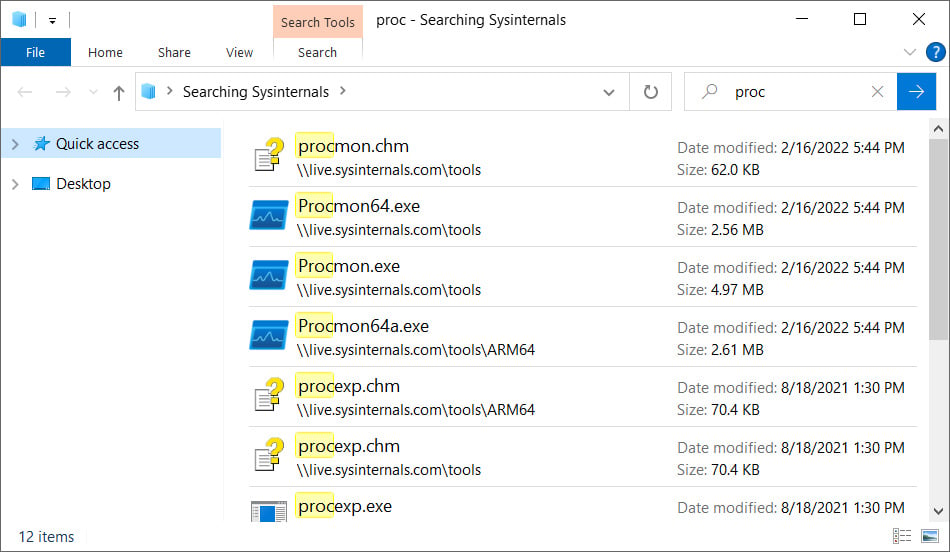
For instance, the common Sysinternals toolset allows you to remotely mount dwell.sysinternals.com as a network share to launch their utilities. To lookup this distant share and list only files matching a specific title, you could use the next ‘search-ms’ URI:
look for-ms:query=proc&crumb=locale:{5376dfc28cf0a7990a1dde1ec4d231557d3d9e6448247a9e5e61bb9e48b1de73}5C{5376dfc28cf0a7990a1dde1ec4d231557d3d9e6448247a9e5e61bb9e48b1de73}5Clive.sysinternals.com&displayname=Seeking{5376dfc28cf0a7990a1dde1ec4d231557d3d9e6448247a9e5e61bb9e48b1de73}20SysinternalsAs you can see from the command higher than, the research-ms ‘crumb’ variable specifies the site to look for, and the ‘displayname’ variable specifies the lookup title.
A custom made search window will look when this command is executed from a Operate dialog or website browser address bar on Home windows 7, Windows 10, and Windows 11, as shown beneath.
Resource: BleepingComputer
Detect how the window title is established to the ‘Searching Sysinternals’ display screen identify we specified in the lookup-ms URI.
Risk actors could use this identical tactic for destructive assaults, where by phishing e-mail are sent pretending to be protection updates or patches that will need to be set up.
They can then established up a distant Windows share that can be employed to host malware disguised as security updates and then include the look for-ms URI in their phishing attachments or emails.
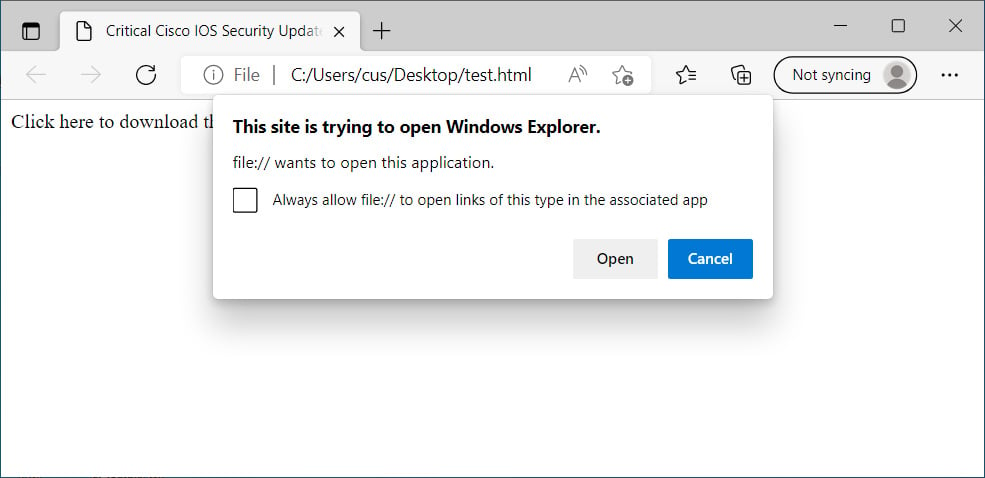
On the other hand, it would not be effortless to get a user to click on a URL like this, specially when it displays a warning, as demonstrated down below.
Source: BleepingComputer
But Hacker Household co-founder and safety researcher Matthew Hickey found a way by combining a freshly uncovered Microsoft Business office OLEObject flaw with the look for-ms protocol handler to open up a distant search window simply just by opening a Term document.
Microsoft Office takes it to the following degree
This week, researchers uncovered that threat actors ended up employing a new Windows zero-day vulnerability in Microsoft Home windows Guidance Diagnostic Resource (MSDT). To exploit it, threat actors created malicious Word paperwork that released the ‘ms-msdt’ URI protocol handler to execute PowerShell commands merely by opening the doc.
Recognized as CVE-2022-30190, the flaw will make it doable to modify Microsoft Workplace paperwork to bypass Protected See and start URI protocol handlers without having conversation by people, which will only direct to additional abuse of protocol handlers.
This was found yesterday when Hickey converted current Microsoft Term MSDT exploits to use the look for-ms protocol handler we described previously.
With this new PoC, when a person opens a Term document, it will immediately start a ‘search-ms’ command to open a Windows Lookup window that lists executables on a remote SMB share. This share can be named what ever the danger actor desires, this kind of as ‘Critical Updates,’ prompting the users to put in the listed malware.
Microsoft Business research-ms: URI handler exploitation, requires person-interaction. Unpatched. pic.twitter.com/iYbZNtMpnx
— hackerfantastic.crypto (@hackerfantastic) June 1, 2022
Like the MSDT exploits, Hickey also showed that you could generate RTF versions that mechanically open up a Windows Search window when the doc is rendered in the Explorer preview pane.
In this article is the exact look for-ms assault being leveraged through an RTF document when Home windows Preview Pane is enabled… -) pic.twitter.com/AmOeGWltjm
— hackerfantastic.crypto (@hackerfantastic) June 1, 2022
By applying this sort of malicious Phrase doc, menace actors can generate elaborate phishing strategies that instantly launch Windows Lookup home windows on recipients’ units to trick them into launching malware.
While this exploit is not as serious as the MS-MSDT remote code execution vulnerability, it could direct to abuse by industrious danger actors who want to generate sophisticated phishing campaigns.
Even though we have presently observed techniques danger actors could exploit this new flaw in the wild, we are not going to share this info for obvious good reasons.
To mitigate this vulnerability, Hickey states you can use the same mitigation for ms-msdt exploits – delete the search-ms protocol handler from the Windows Registry.
- Run Command Prompt as Administrator.
- To again up the registry key, execute the command “reg export HKEY_Classes_ROOTsearch-ms look for-ms.reg“
- Execute the command “reg delete HKEY_Lessons_ROOTsearch-ms /f“
A Windows ProtocolNightmare
Equally the MSDT and search-ms abuse illustrations are not new, to begin with disclosed by Benjamin Altpeter in 2020 in his thesis about Electron application protection.
Nonetheless, it was not until finally lately that they started off to be weaponized in Word paperwork for phishing attacks with no user interaction, which turned them into zero-working day vulnerabilities.
Dependent on Microsoft’s steering for CVE-2022-30190, the organization seems to be tackling the flaws in the protocol handlers and their underlying Windows features, alternatively than the reality that danger actors can abuse Microsoft Office environment to start these URIs devoid of person interaction.
As CERT/CC vulnerability analyst Will Dormann suggests, these exploits essentially make the most of two different flaws. With out correcting the Microsoft Office URI concern, even more protocol handlers will be abused.
Hickey also informed BleepingComputer that he thinks that this not automatically a flaw in the protocol handlers, but alternatively a combination leading to a ‘Microsoft Business OLEObject lookup-ms Place Route Spoofing Vulnerability.’
“The next very best factor is to correct the research talents title and area placing messages to prevent these kinds of spoofing assaults or disable it as a URI handler,” explained Hickey in a conversation about the flaws.
In June, scientists unintentionally disclosed the technological particulars and a proof-of-strategy (PoC) exploit for a Home windows Spooler RCE vulnerability named PrintNightmare.
Although the RCE component was swiftly preset, a broad vary of community privilege elevation vulnerabilities have been identified that continued to be disclosed beneath the ‘PrintNightmare’ classification.
It was not till Microsoft designed some drastic modifications to Windows Printing that they eventually obtained manage of this vulnerability course, even nevertheless it caused numerous printing problems for some time.
By tackling the issue only at the protocol handler/Home windows feature side, Microsoft is experiencing a total new ‘ProtocolNightmare’ classification where by scientists will keep on to find new URI handlers to abuse in assaults.
Until eventually Microsoft helps make it not possible to start URI handlers in Microsoft Office without having person conversation, be geared up for a full sequence of related information articles or blog posts as new exploits are introduced.
Microsoft sent us the adhering to statement when requested how they prepared on resolving this issue.
“This social engineering approach requires a user to run a malicious document and interact with a checklist of executables from an attacker specified network share. We suggest customers practice safe and sound computing habits and to only open information that arrive from trustworthy sources.” – a Microsoft spokesperson.