New Malvertising Campaign via Google Ads Targets Users Searching for Popular Software

Customers browsing for well-liked program are getting focused by a new malvertising marketing campaign that abuses Google Advertisements to provide trojanized variants that deploy malware, such as Raccoon Stealer and Vidar.
The action would make use of seemingly credible web sites with typosquatted domain names that are surfaced on top of Google lookup benefits in the variety of destructive ads by hijacking lookups for certain keyword phrases.
The best objective of this kind of assaults is to trick unsuspecting customers into downloading malevolent packages or possibly undesirable applications.
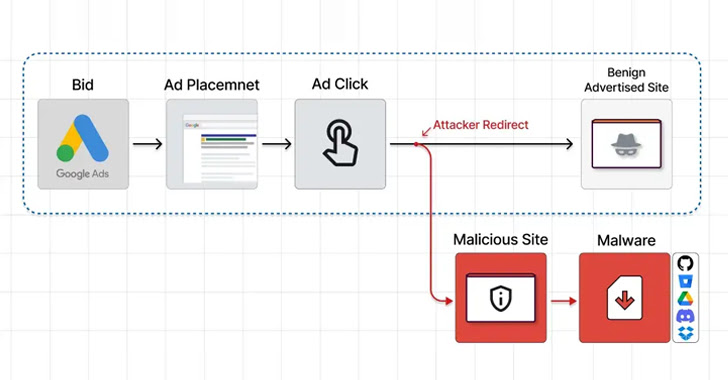
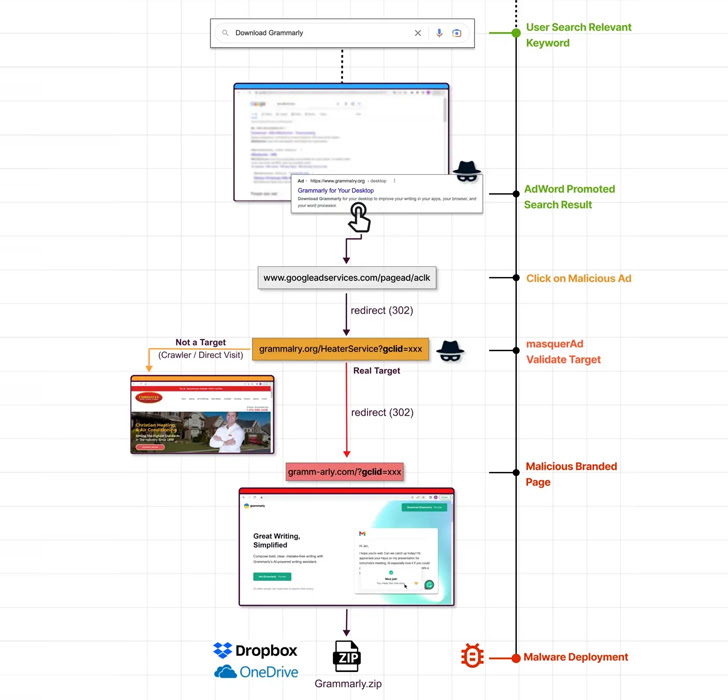
In a person marketing campaign disclosed by Guardio Labs, risk actors have been observed generating a community of benign websites that are promoted on the search engine, which when clicked, redirect the visitors to a phishing page that contains a trojanized ZIP archive hosted on Dropbox or OneDrive.
“The moment these ‘disguised’ web pages are becoming visited by qualified site visitors (these who actually click on on the promoted lookup consequence) the server instantly redirects them to the rogue web-site and from there to the malicious payload,” researcher Nati Tal reported.
Amid the impersonated software program consist of AnyDesk, Dashlane, Grammarly, Malwarebytes, Microsoft Visible Studio, MSI Afterburner, Slack, and Zoom, among many others.
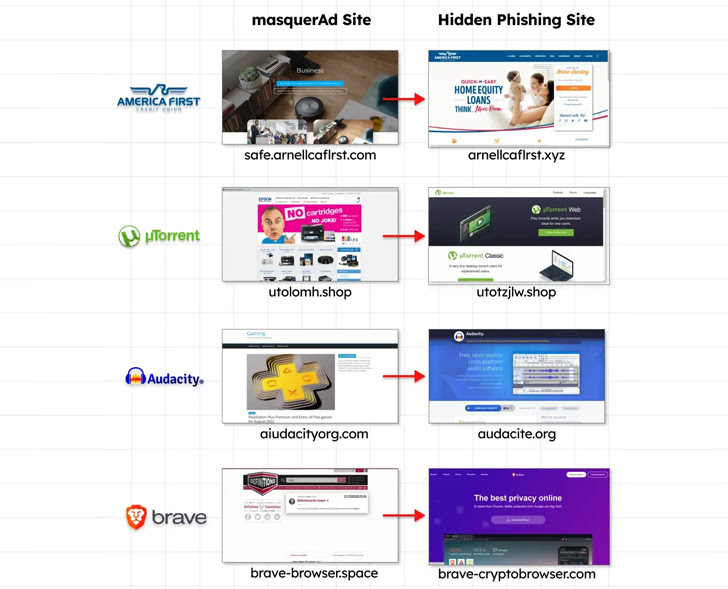
Guardio Labs, which has dubbed the campaign MasquerAds, is attributing a massive chunk of the activity to a risk actor it is monitoring underneath the identify Vermux, noting that the adversary is “abusing a wide checklist of models and keeps on evolving.”
The Vermux operation has generally singled out people in Canada and the U.S., utilizing masquerAds web sites customized to queries for AnyDesk and MSI Afterburner to proliferate cryptocurrency miners and Vidar facts stealer.
The improvement marks the ongoing use of typosquatted domains that mimic authentic application to entice people into setting up rogue Android and Windows apps.
It’s also significantly from the initial time the Google Advertisements system has been leveraged to dispense malware. Microsoft last thirty day period disclosed an attack marketing campaign that leverages the promoting assistance to deploy BATLOADER, which is then applied to fall Royal ransomware.
BATLOADER apart, destructive actors have also utilised malvertising methods to distribute the IcedID malware by means of cloned net internet pages of nicely-identified programs this sort of as Adobe, Courageous, Discord, LibreOffice, Mozilla Thunderbird, and TeamViewer.
“IcedID is a noteworthy malware spouse and children that is able of delivering other payloads, which include Cobalt Strike and other malware,” Development Micro claimed past 7 days. “IcedID allows attackers to perform really impactful abide by as a result of attacks that direct to whole system compromise, these as data theft and crippling ransomware.”
The results also appear as the U.S. Federal Bureau of Investigation (FBI) warned that “cyber criminals are making use of research engine advertisement products and services to impersonate brands and immediate people to malicious websites that host ransomware and steal login credentials and other economic information.”

