GuLoader Malware Utilizing New Techniques to Evade Security Software

Cybersecurity researchers have uncovered a huge selection of tactics adopted by an innovative malware downloader called GuLoader to evade protection software program.
“New shellcode anti-investigation method makes an attempt to thwart researchers and hostile environments by scanning entire approach memory for any digital equipment (VM)-relevant strings,” CrowdStrike researchers Sarang Sonawane and Donato Onofri stated in a technological produce-up printed past week.
GuLoader, also called CloudEyE, is a Visual Standard Script (VBS) downloader that is utilized to distribute distant access trojans these types of as Remcos on infected devices. It was to start with detected in the wild in 2019.
In November 2021, a JavaScript malware strain dubbed RATDispenser emerged as a conduit for dropping GuLoader by signifies of a Base64-encoded VBScript dropper.
A recent GuLoader sample unearthed by CrowdStrike exhibits a three-stage procedure wherein the VBScript is developed to deliver a upcoming-phase that performs anti-analysis checks before injecting shellcode embedded within just the VBScript into memory.
The shellcode, in addition to incorporating the similar anti-investigation strategies, downloads a final payload of the attacker’s option from a remote server and executes it on the compromised host.
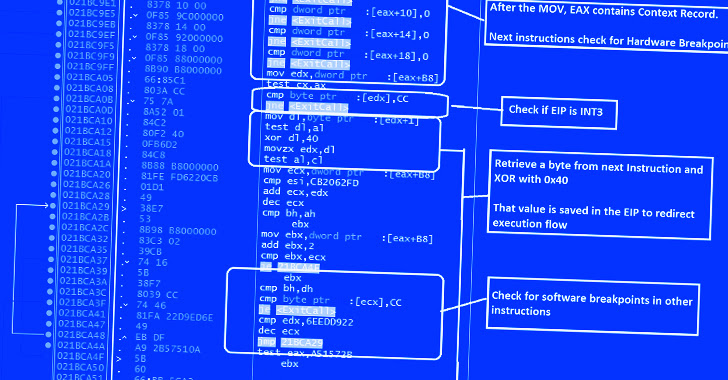
“The shellcode employs quite a few anti-assessment and anti-debugging tips at each and every step of execution, throwing an error message if the shellcode detects any known investigation of debugging mechanisms,” the researchers pointed out.
This incorporates anti-debugging and anti-disassembling checks to detect the existence of a remote debugger and breakpoints, and if found, terminate the shellcode. The shellcode also capabilities scans for virtualization computer software.
An additional ability is what the cybersecurity business calls a “redundant code injection system” to steer clear of NTDLL.dll hooks carried out by endpoint detection and response (EDR) methods.
NTDLL.dll API hooking is a system used by anti-malware engines to detect and flag suspicious procedures on Home windows by checking the APIs that are regarded to be abused by risk actors.
In a nutshell, the strategy entails making use of assembly recommendations to invoke the important home windows API perform to allocate memory (i.e., NtAllocateVirtualMemory) and inject arbitrary shellcode into that place by way of course of action hollowing.
https://www.youtube.com/check out?v=5LudHSojlXA
The findings from CrowdStrike also occur as cybersecurity organization Cymulate shown an EDR bypass strategy identified as Blindside that enables for running arbitrary code by working with hardware breakpoints to produce a “course of action with only the NTDLL in a stand-by itself, unhooked point out.”
“GuLoader stays a hazardous risk that is been regularly evolving with new solutions to evade detection,” the researchers concluded.

